This guide will walk you through securing your Nginx server with Basic Authentication. By implementing basic auth, you can restrict access to authorized users only, protecting your server from unauthorized modifications or breaches. Basic Authentication is a straightforward method that demands username and password verification for users attempting to access your server. This layer of security helps in safeguarding your server against unauthorized access, modifications, or potential breaches.
Step 1: Install Apache Utilities
The first step involves installing the apache2-utils package, which contains the htpasswd utility used to create and manage the password file for Basic Authentication.
Open a terminal or SSH into your server and execute the following command:
sudo apt-get install apache2-utilsStep 2: Create a User
Next, you will create a user with a password that will be stored in the .htpasswd file. This file is referenced by Nginx to authenticate users.
To create a user named foobar, execute the following command:
sudo htpasswd -c /etc/nginx/.htpasswd foobarYou will be prompted to enter and confirm a password for the user foobar. The -c option creates the .htpasswd file. If you're adding additional users, omit the -c option to avoid overwriting the file.
Step 3: Configure Nginx for Basic Authentication
Now, it's time to configure your Nginx server to require Basic Authentication for access.
- Open the Nginx configuration file for your website located at
/etc/nginx/sites-enabled/your_site_namewith your preferred text editor. If you're usingnano, the command would look like this:sudo nano /etc/nginx/sites-enabled/your_site_name - Within the
serverblock of your configuration, add the following lines to enable Basic Authentication:
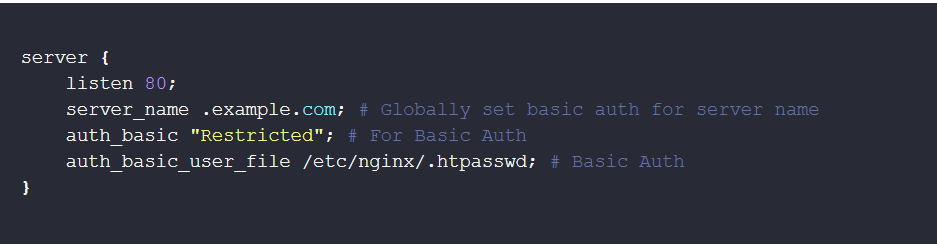
server {
listen 80;
server_name .example.com; # Globally set basic auth for server name
auth_basic "Restricted"; # For Basic Auth
auth_basic_user_file /etc/nginx/.htpasswd; # Basic Auth
}This configuration prompts users for a username and password when accessing any part of the site.
Step 4: Reload Nginx Configuration
After modifying the Nginx configuration, you must reload Nginx to apply the changes:
sudo service nginx reloadOr, if you're using systemd:
sudo systemctl reload nginxThis command reloads the Nginx configuration without interrupting the running service.
Conclusion
You have successfully secured your Nginx server with Basic Authentication. Only users who provide a valid username and password can access your site, enhancing its security against unauthorized access. Remember to manage the .htpasswd file carefully, adding or removing users as necessary to maintain your site's security.
While Basic Auth offers a simple way to secure your Nginx server, it has its limits.
You need to understand that the usernames and passwords are transmitted in Base64 encoding, easily decoded. While this isn't ideal, if your website uses HTTPS, the overall communication channel is encrypted, protecting the credentials from eavesdroppers (anyone intercepting the communication). You might want to read my guide for full encryption for nginx and apache server. For a local development, learn more about setting up HTTPS for local development.